In an ultimate couple of months, there was an immeasurable increase in smartphones and tablets within the cellular marketplace. The slew of capabilities offered by way of carriers has contributed to making these gadgets pervasive within the company environment. Which cellular smartphone running gadget has invaded your corporate sphere? Is it an iOS Phone, an Android telephone, a Windows Mobile 7, or a BlackBerry? Is it they all or two or more device running systems? If so, has your enterprise embraced a Mobile Device Management answer?
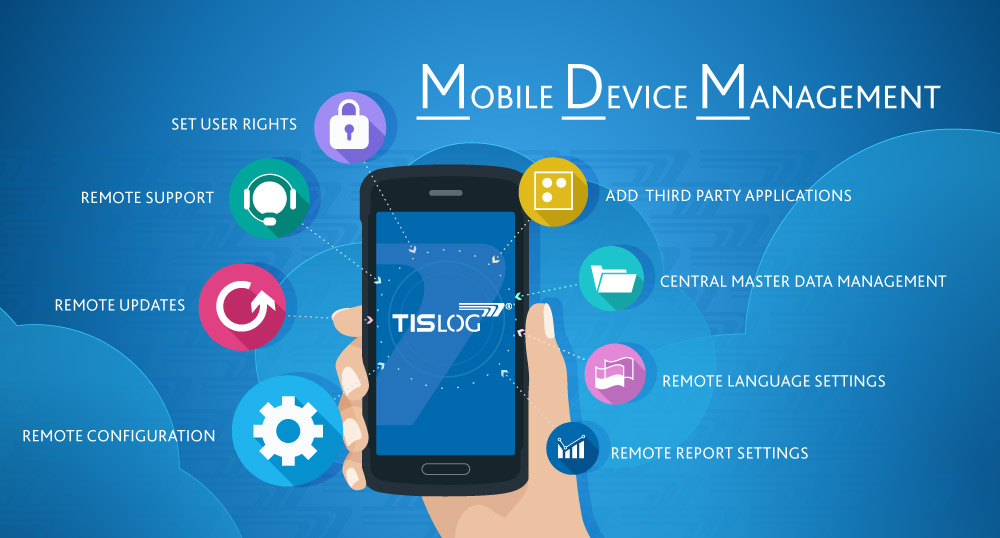
What does an MDM solution deliver?
As new mobile platforms preserve rising, supporting and managing them has ended up a Herculean task. Mobile Device Management is not a ‘first-rate to have device’; it has emerged as necessary. Some of the common capabilities expected from an MDM platform are:
A single and centralized console for managing extraordinary sorts of mobile endpoints, helping each Corporate provided and Employee-owned devices
The capacity to gather stock and security compliance information from the cellular endpoints after which offer reports
The enforcement of fundamental device safety rules like Password, Encryption, Restrictions, and execution of far off moves like Approve, Block, Wipe the device
Why should you embrace MDM from the cloud?
READ MORE :
- Mobile App Vs. Website for ECommerce
- Samsung D900 and Samsung E900 Two Brilliant Samsung Mobile Phones
- 9 Tips For Optimizing Your Blog For Mobile Devices
- Sony C905 Joins the Sony Ericsson Cybershot Range
- Fundamentals of Mobile Website Development (and Tips on How to Work on These)
An in-residence MDM answer requires both operational and infrastructure investment. Furthermore, the workforce and assets want to be allocated up the front for setting up the servers and community and schooling the workforce on the new MDM platform for coping with the gadgets. An MDM answer from the cloud lets you pass this dilatory system by using the infrastructure and management answer hosted in the cloud.
This fosters easy and quick consumer onboarding methods and eliminates the want for extra hardware and staff funding. It speeds up the implementation and will increase user productiveness by using growing reliability, scalability, and safety. A cloud-based solution additionally allows IT administrators to manipulate those gadgets from anywhere in a secured manner from a single window.
Mobile gadgets have endured to the upward thrust of their popularity, and the adoption charges are extremely high. This arises from the fact that mobile communication has come to be an everyday affair. For many people, leading an existence without a mobile cellphone might be almost not possible for a lot of us to tolerate.
Our lives are dependent on the devices for so many matters besides the predominant advantage of imparting a way of verbal exchange with people. Again the continuing upward push in the level of adoption of devices has been observed by sophistication inside the devices and their models and the level of capability possible with the devices.
There are now smartphones and drugs based totally on numerous one-of-a-kind structures depending on the manufacturer. This has elevated the functionality that may be carried out with the cellular phones to unimaginable ranges, and that is continuing with increasing portions getting added to the gadgets. The smartphones and tablets accompany customers anywhere and anywhere they pass and in everything that they do.
Mobile phones now have access to the net at first-rate speeds and with extensive functionality, helping customers get entry to records and even manage the statistics. With such functionality, the cell telephones and devices are adding an entire one-of-a-kind perspective to the equation. This is IT security. The devices had been a considerable risk, which has to do with the reality that people can get admission to many sources from their telephones. The mobile devices are a hazard to the statistics stored in them and the networks wherein they may be a part.
In a way, just like the way humans take some comprehensive steps to comfortable their computers, the cell devices have to be secured. This arises from the truth that the information and records accessed and contained in them consist of non-public and private records, snapshots and contacts, and even facts and safety information belonging to monetary debts and different on-line companies.
The gadgets, being the lifeline that they have got come to be, require protection to manage and avert the dangers and threats available. A look at the stairs to install vicinity to make certain that cellular security is guaranteed could help many customers of the cell devices.
The first actual step needs to be locating the gadgets that have fine or above average safety features whilst compared to different gadgets inside the marketplace. This mitigates the risks accessible, and security features are one-of-a-kind depending on the manufacturer and the centered customers with the unique device.
A foremost hazard to mobile devices’ safety is the third-party software, which may also come with connected scripts by cybercriminals whose purpose of getting control over your tool. Therefore, pass for the signed 1/3 birthday celebration apps to ensure authenticity and restrict the level to which the other human beings can arbitrarily set up those third birthday celebration apps and inadvertently gain manage for your device also directly to the commercial enterprise or company community.
For functions of having access to the net thru any of the cell gadgets, it’s far critical to guarantee safety through the permitting of encryption and authentication. Encryption is feasible with the gadgets that have been manufactured with sturdy protection controls and are there to be used. It is simplest that any person might be assured of the safety of any sensitive statistics get admission to from the device.
Authentication will improve protection with smartphones and the capsules, specifically if the device is lost or falls into the incorrect arms. This additionally ensures that data will not fall into the hands of criminals or simply some other character. And it’s far nevertheless on this point that the usage of the Remote Wipe Capabilities suffices so that in the occasion that the device is stolen, then the customers of the tool can remotely get right of entry to and disable the devices within the occasion that the gadgets are misplaced or stolen.

